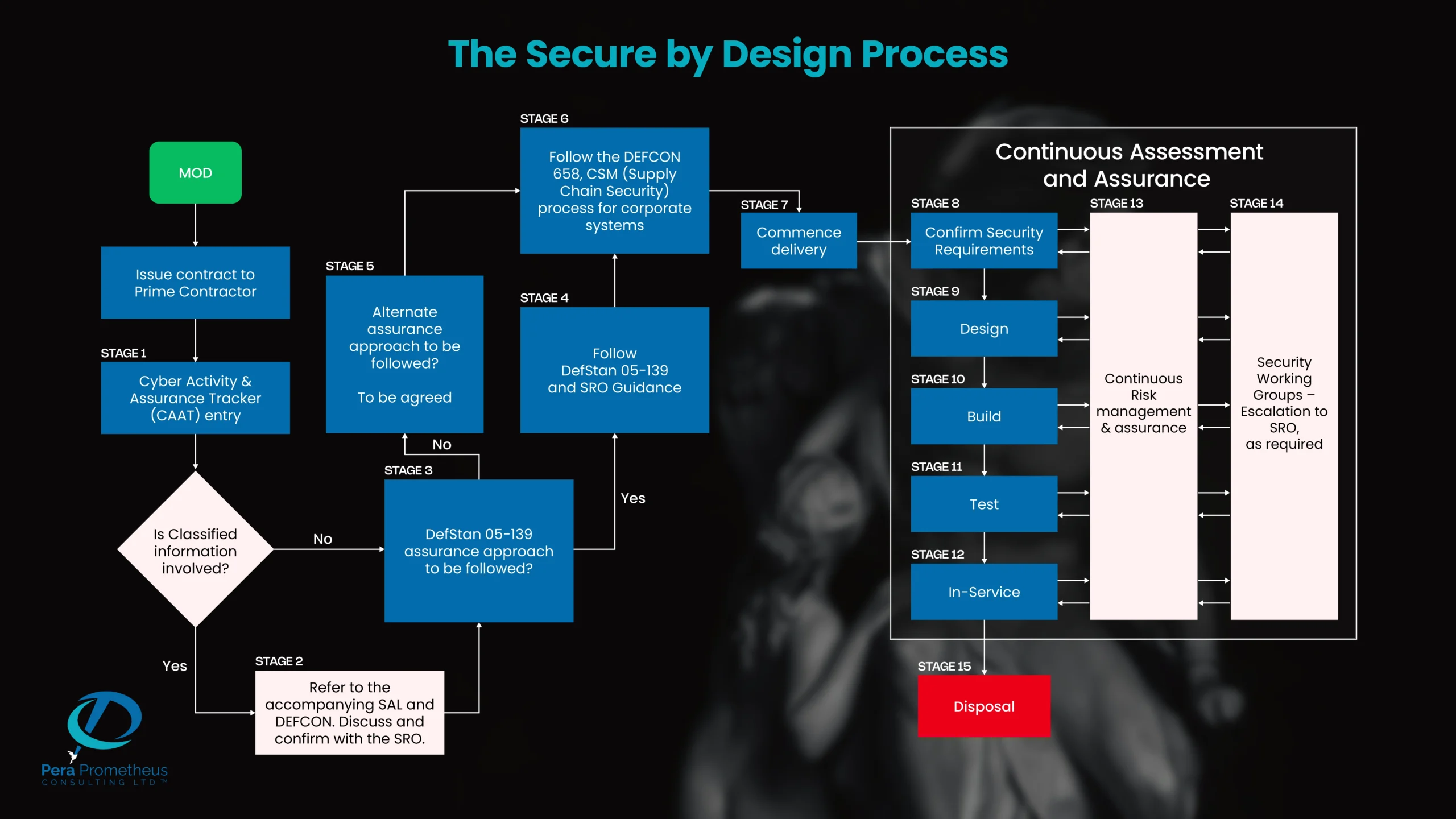
Stage 1
Cyber Activity and Assurance Tracker (CAAT) – This is where the Secure by Design approach, starts (What is Secure by Design?). It is useful to remember why Secure by Design is used to maintain focus and relevance through the development of Products, Services or Solutions (PSS)
Completing the CAAT is an MOD responsibility but is likely to require input from the supplier to answer some of the questions as development of the Product, Solution or Service progresses. The purpose of the CAAT is to track progress of security issues and operations through the development of the PSS. CySAAS will refer to the CAAT when they perform their project and programme audits.
Classified information i.e. OFFICIAL, OFFICIAL-SENSITIVE, SECRET and TOP SECRET is dealt with slightly differently from a policy perspective, although some of the controls to secure Classified information may be relevant to the SbD assurance approach. This to be agreed with the Senior Risk Owner (SRO).
Instructions and guidance for securing and managing Classified information are contained in the Security Aspects Letter (SAL) related to the contract as well as Defence Conditions (DEFCONs). For OFFICIAL-SENSITIVE information, DEFCON 660 applies and for SECRET information, DEFCON 659A applies.
If in doubt, discuss this with the SRO when you discuss the preferred assurance approach to be followed.
Stage 3
Senior Risk Owner, Agreed Assurance Route – It is essential the SRO is engaged to understand and define the context behind why the product, service or solution is being procured . This is important to correctly assess and devise mitigation strategies for identified risks associated with the use of the Product Service or Solution PSS and is all part of planning the security activities which includes planning the through-life approach. At this stage, the identification of other key stakeholders will also begin.
Equally important is to agree an appropriate strategy to be followed, with the SRO. One that meets their requirements as to what artefacts and other evidence is needed to meet their assurance requirements for the Product, Service or Solution (PSS) they are procuring.
Stage 4
Follow DefStan 05-139 assurance and SRO Guidance – It is likely the agreed assurance pathway, for the majority of engagements, to define security controls will be to follow that set out in DefStan 05-139, supplemented by SRO guidance and direction. A copy of DefStan 05-139 can be found on the Knowledge in Defence website - Knowledge in Defence (KiD).
Stage 5
Alternatively, the SRO may decide a different assurance approach, for their particular procurement activity, is required. For example, NIST 800-171 is typically applied to Information Technology systems. However, for Operational Technology (OT) based systems, NIST 800-82 may be a more appropriate standard for the PSS being delivered to MOD. This is a decision for the Contracting Authority SRO.
Stage 6
Whatever the assurance approach that is decided upon for the Product, Service or Solution (PSS) that is being delivered, remember, the CSM DefStan 05-138 Cyber Risk Profile Level controls will also need to be applied to the corporate infrastructure. Refer to the Cyber Security Model for more information on this.
While the SbD assurance process requires considerations to be made around Cyber supply chain security, these are specific to the PSS being produced and delivered. DEFCON 658 and DefStan 05-138 is a more general approach to securing the MOD supply chain and yes, there will invariably be commonality between the controls applied to the organisation and those required for the PSS.
Note: DefStan 05-138 controls used to apply to systems handling or processing MOD Identifiable Information but, issue 4 of DefStan 05-138 has extended this across the corporate environment to ensure organisational security and resilience.
Stage 7
Through Life Approach - Whatever the assurance pathway that is agreed with the SRO, a through life approach will be planned.
Stage 8
Confirm Security Requirements – It is important to confirm the Authorities identified security requirements for the Product, Service or Solution (PSS) are still valid. It is not unusual for some procurement activities to take a long time to complete before contract award takes place and during this time, a lot can change. This is particularly true of Cyber where new vulnerabilities and risks are identified by the minute, or so it seems.
Confirming security requirements are still valid and planning security activities at this stage is important so as not to waste time and effort.
Stage 10
Build – Assure, verify and test as part of Product, Service or Solution (PSS) build activities. This is an essential part of collating assurance evidence for the SRO.
Stage 11
Test – Assure, verify and test as part of Product, Service or Solution (PSS) build activities. This is an essential part of collating assurance evidence for the SRO
Stage 12
In service – Once final acceptance of the Product, Service or Solution (PSS) is given, by the SRO. Do not forget that engagement with and management of the supply chain is an integral part of ongoing, through life PSS management.
Stage 13
Continuous risk management and assurance – Effective Secure by Design relies upon a robust, through life, risk management approach. The corner stone of this is the governance applied through the Security Working Groups which are management meetings held, typically, quarterly. At each SWG risk reviews are made, programme progress is measured and risks & vulnerabilities tracked with mitigation work being assessed.
Do not forget to inform key stakeholders on progress, issues and incidents.
Stage 14
Continuous risk management and assurance – Effective Secure by Design relies upon a robust, through life, risk management approach. The corner stone of this is the governance applied through the Security Working Groups which are management meetings held, typically, quarterly. At each SWG risk reviews are made, programme progress is measured and risks & vulnerabilities tracked with mitigation work being assessed.
Do not forget to inform key stakeholders on progress, issues and incidents.
Stage 15
Disposal – Perhaps the most often overlooked stage of any procurement process is how to dispose of Product, Service or Solution (PSS) once they reach their end of life. This is particularly important with regards to any classified (OFFICIAL, SECRET etc.) assets that are associated with or comprise part of the PSS. Particular requirements, concerning the safe and secure disposal of equipment to be agreed with the SRO and documented.
At Pera Prometheus, we are committed to making the journey to compliance as smooth and transparent as possible. To help navigate the recent surge in regulatory requirements and answer common questions, we have developed a clear, interactive process map designed specifically for SMEs.
Explore Each Stage: Click on the individual nodes within the flowchart to expand detailed information for that phase.
Within the information boxes, you will find external links to official resources and documentation where required.
We strive for absolute accuracy. If your specific experience differs from this map, or if you require a deeper consultation tailored to your business, please notify us.