Table of Contents
The UK government has recently announced a public consultation seeking views on three proposals aimed at striking a significant blow to the ransomware criminal business model. As outlined by the National Cyber Security Centre (NCSC), the consultation will consider three proposals:
- A targeted ban on ransomware payments for all public sector bodies and critical national infrastructure (CNI).
- A ransomware payment prevention regime.
- A mandatory reporting regime for ransomware incidents.
The ultimate goal is to protect UK CNI and the broader economy from the devastating impact of ransomware. The public can provide their views on the proposed consultation until 5 pm, 8 April 2025, via GOV.UK.
Why This Initiative Matters
Ransomware attacks have caused major disruptions in the UK and globally, affecting critical services like healthcare and transport. Globally, a 2023 survey revealed that 46% of organisations were hit by ransomware in the past year, with average downtime lasting 16 days. In the UK, the NHS’s WannaCry attack in 2017 cost over £92 million in recovery and lost productivity. Many organisations have paid ransoms averaging over £200,000, with some facing even higher costs as most incidents go unreported.
Transparency surrounding cyber attacks is a huge issue. Organisations cover up cyber attacks to protect their reputation, but this leads to no one learning from them, increasing the success rate for criminals. The government aims to combat this by banning ransom payments by public sector organisations, mandating ransomware incident reporting, and using this data to prevent future attacks and reduce financial incentives for criminals.
Evolution of Ransomware Attacks
As the government ramps up efforts to crack down on ransomware attacks, the threat itself is evolving rapidly, becoming more sophisticated and organised. One concerning trend is the rise of Ransomware-as-a-Service (RaaS). This model allows inexperienced hackers to launch attacks using pre-built ransomware tools, significantly lowering the barrier to entry for cybercrime.
A white paper published in September 2023 by NCSC and the National Crime Agency (NCA) highlights that various phases of ransomware attacks are conducted by different cyber criminals using RaaS. The document also states that most ransomware incidents occur not because of sophisticated attacks, but due to poor cyber hygiene and security flaws in modern IT systems.
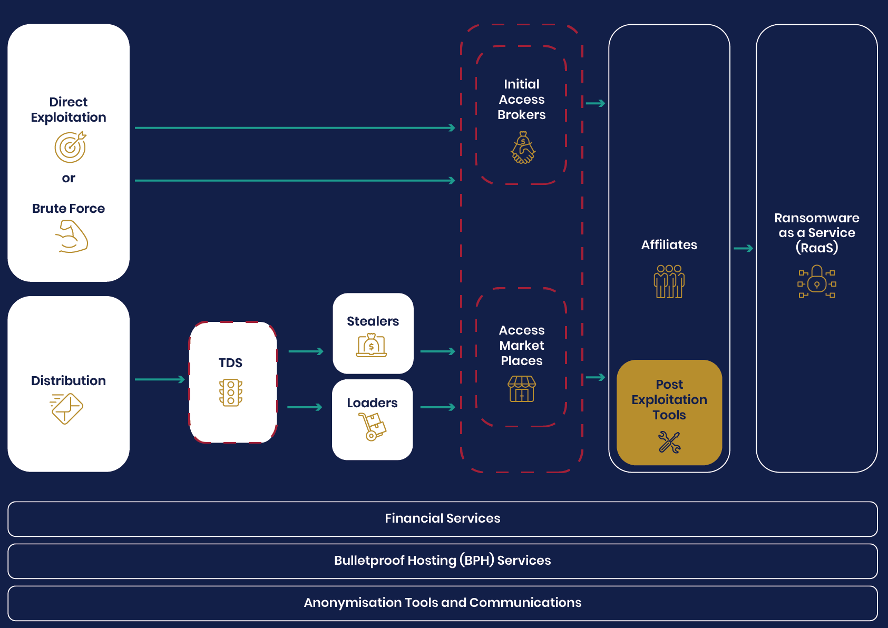
Figure: Common initial vectors (NCSC)
Building Ransomware Resilience
With the increased ransomware attack, the top priority for any organisation or business should be prevention. Every organisation should conduct a Business Impact Analysis (BIA) to ensure they are ransomware resilient. A BIA is a key process that helps organisations identify and understand how cyber threats, like ransomware, could disrupt their operations. It enables them to assess the impact on important business functions, prioritise recovery efforts, conduct regular backups, and allocate resources effectively to minimise damage.
NCSC’s guidance on ransomware-resistant backups provides straightforward advice to strengthen organisations against attacks. Key steps include:
- Immutable Backups: Use backups that cannot be changed or deleted by ransomware.
- Separation from the Network: Keep backups offline or in secure cloud environments with limited access.
- Regular Testing: Frequently check backups to ensure they work and can restore data quickly if needed.
Our Opinion on the Proposal
- Targeted Ban on Ransomware Payments for Public Sector Bodies and CNI: Although the goal is to remove the financial motivation for attackers by making these organisations less attractive to cyber criminals, this could have some adverse effects, like, the focus may shift more on private businesses who might pay, more aggressive tactics like releasing sensitive data may be used and recovery time could be longer without payment.
- Ransomware Payment Prevention Regime: This aims to help the National Crime Agency (NCA) monitor live attacks and ransom demands, guide victims on how to respond, and block payments to known criminal groups or sanctioned entities. This is a positive step by the government, but businesses must also strictly follow cyber resilience guidance. Without compliance, the NCA may struggle to handle an increase in attacks.
- Mandatory Reporting Regime for Ransomware Incidents: In our opinion, this is the cornerstone of the government’s strategy. When organisations promptly report ransomware incidents, it enables authorities to analyse attack methods and patterns, share actionable intelligence with other potential targets, and coordinate responses to mitigate damage and prevent further attacks. It also helps law enforcement trace and prosecute cybercriminals, disrupting their operations over time.
Conclusion
The government has increased its efforts to tackle the ransomware issue, but success will require collaboration across public and private sectors. Organisations must adopt best practices for cybersecurity and backup management while supporting governmental efforts to disrupt ransomware networks. Together, these actions can build a more secure digital environment for all.
Express your opinion on GOV.UK.




