Table of Contents
Introduction
No defence is 100% guaranteed and at the early stages of an organisation’s information and cybersecurity roadmap all are vulnerable but, knowing how to respond to an incident can minimise its impact. An organisation that responds well to an incident may be viewed positively by external observers. This is why effective incident management processes within an organisation are essential. Managing security incidents requires a structured approach to identifying, responding to, and mitigating threats. This ensures timely detection, response, and recovery from incidents that may disrupt business operations. A well-defined incident management process helps maintain business continuity, minimises damage, and strengthens resilience.
In May 2023, the Cl0p ransomware group exploited a zero-day vulnerability (CVE-2023-34362) in MOVEit Transfer, affecting 2,500+ organisations and 100 million individuals, including BBC, British Airways, and U.S. government agencies. The breach exposed sensitive personal and financial data, prompting rapid response efforts. Progress Software issued patches, while CISA and Mandiant assisted in containment. Organisations applied incident management strategies like disabling affected systems, enhancing monitoring, and enforcing security updates. This 2023 MOVEit data breach highlighted the critical role of incident management in information and cybersecurity.
What is Incident Management?
Incident management is the systematic process of identifying, analysing, containing, eradicating, and learning from security incidents. It involves a proactive approach to handling threats such as malware infections, phishing attacks, data and security breaches before they escalate into full-scale crisis.
Building on this proactive approach, a well-defined incident management strategy sets clear goals and implements an effective incident response framework. The goals of incident management are:
- Quick Detection: Rapid identification of security threats.
- Effective Containment: Minimising the impact of incidents on systems and data.
- Efficient Eradication: Removing the root cause to prevent recurrence.
- Swift Recovery: Restoring normal operations with minimal downtime.
- Post-Incident Review: Learning from incidents to improve future security measures.
Key Components of Incident Management:
To achieve these incident management goals, an organisation needs to implement an effective framework and have key components to ensure they can respond swiftly and efficiently to security incidents. These elements help maintain security, minimise damage, and support recovery efforts:
- Incident Response Team (IRT): A specialised team responsible for handling security incidents.
- Incident Response Plan (IRP): A documented strategy that outlines the steps to manage security breaches.
- Communication Protocols: Ensuring effective coordination between internal teams and external stakeholders.
- Continuous Monitoring: Leveraging security tools to detect anomalies and threats.
Types of Information Security Incidents
Effective incident management begins with understanding potential security threats. Organisations must recognise these threats to build robust defences and develop effective response plans. Each type of incident presents unique risks and consequences, making awareness essential for implementing stronger prevention and mitigation strategies. Some of the most common incidents in today’s digital landscape include:
- Malware Attacks. Viruses, ransomware, and spyware designed to compromise systems.
- Phishing & Social Engineering. Deceptive tactics to manipulate individuals into divulging sensitive information.
- Data Breaches. Unauthorised access leading to data leakage or theft.
- Insider Threats. Malicious or negligent actions by employees compromising security.
- Denial of Service (DoS) Attacks. Overloading systems to disrupt normal operations.
- Zero-Day Exploits. Attacks targeting previously unknown vulnerabilities.
But remember, not all incidents occur in cyber space! Other threats include:
- Environmental Damage. Flooding, fire, storm damage. All of which are capable of disrupting information availability.
- Physical Damage. Either by deliberate acts of vandalism or sabotage, or simply careless work practices, negligence or poor maintenance.
- Loss or Theft. Again, either by wilful acts of espionage or simple carelessness.
Incident Management and Incident Response Processes
When an information or cyber security incident occurs, a swift and effective response is essential to mitigate risks and minimise disruption. Understanding the difference between incident management and incident response ensures that organisations not only react appropriately, but also implement long-term improvements to strengthen security resilience
Incident Management
Incident Management focuses on the broader strategy of handling security incidents within an organisation. It ensures that security threats are identified, documented, and resolved efficiently. A structured incident management approach helps minimise operational disruption and strengthens resilience against information threats. Key aspects of incident management include:
- Developing policies and procedures for incident handling.
- Assigning responsibilities to incident response teams.
- Implementing security measures to prevent incidents.
- Continuously improving security operations based on lessons learned.
Incident Response
Incident Response is a subcomponent of incident management, focusing on the specific steps taken to address security breaches as they occur. This process ensures that threats are contained, mitigated, and resolved effectively by following a structured lifecycle. The incident response lifecycle consists of:
- Triage
- Identify and categorise the incident based on severity and urgency.
- Determine the potential impact on the organisation and prioritise response efforts.
- Analysis
- Investigate the nature and source of the incident using forensic tools.
- Gather relevant data to understand the extent of the compromise.
- Containment/Mitigation
- Implement immediate measures to limit the spread and impact of the incident.
- Isolate affected systems, disable compromised accounts, or block malicious traffic.
- Remediation/Eradication
- Remove the root cause of the incident, such as malware or unauthorised access.
- Apply security patches, update system configurations, and enhance defences.
- Recovery
- Restore normal business operations by reinstating affected systems and data.
- Monitor systems to ensure the threat has been fully neutralised.
- Review
- Conduct a post-incident analysis to document findings and assess response effectiveness.
- Implement lessons learned to refine security policies and improve future response efforts.
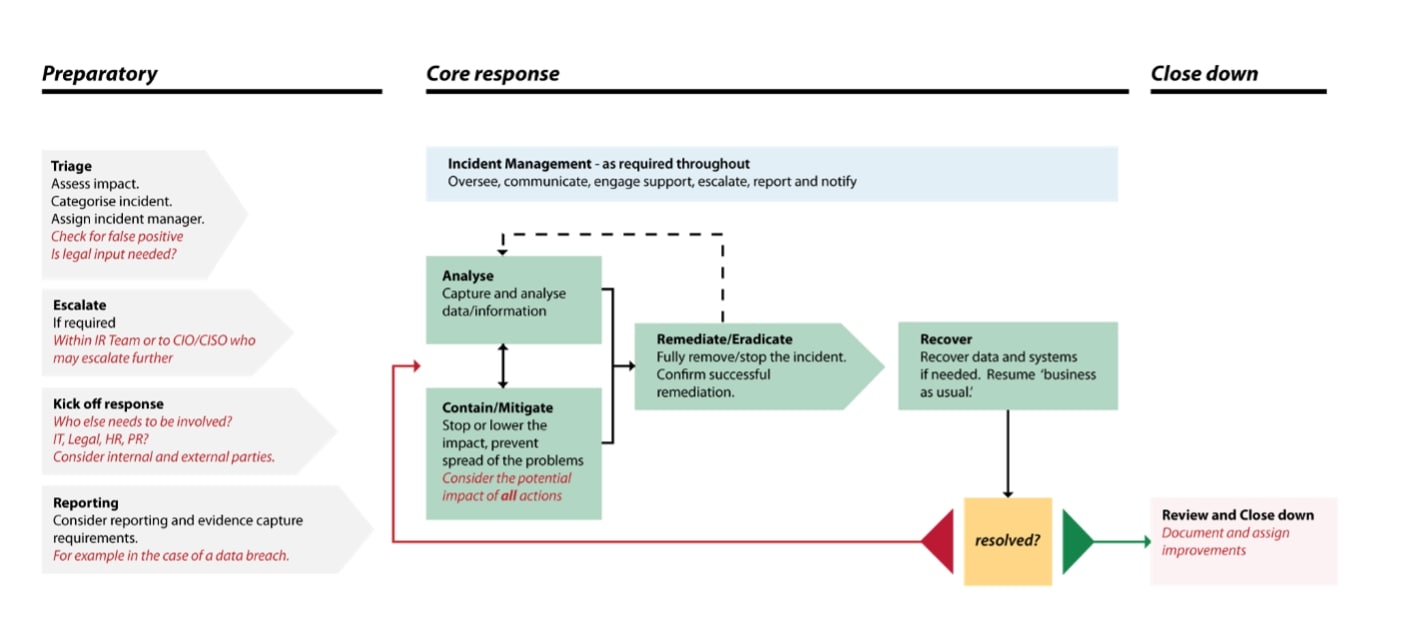
Figure – Incident Response (NCSC)
Key Takeaways
Effective incident management is essential for safeguarding organisations against evolving information and cyber threats.
- Preparation is key. Establish clear policies, train staff, and implement robust monitoring tools.
- Timely response minimises impact. Rapid detection, containment, and mitigation can prevent escalation.
- Continuous improvement strengthens security. Post-incident reviews help refine strategies and enhance resilience.
Investing in proactive incident management and response ensures long-term security and business continuity. Stay informed. Stay protected.
Pera-Prometheus offers expert advice on how to conduct incident management effectively. Whether you’re looking to enhance your response strategies, governance risk and compliance, develop a business continuity plan, or improve information and cyber security risk assessment UK, we can help.




