Table of Contents
Why the necessity?
In today’s digital age, cybersecurity is vital to keeping our Critical National Infrastructure (CNI) safe. The world today relies heavily on a well-functioning Network and Information System (NIS) which plays a vital role in our critical infrastructures like transport, energy supplies, logistics and healthcare. Time and time again, we have experienced numerous cyber security incidents and the chaos that it brought when these NIS were disrupted. Therefore, their reliability and security is critical for a good functioning society.
The National Cyber Security Centre (NCSC) is committed to working with large organisations, SMEs, government agencies, the general public and departments to ensure national critical NIS are subject to effective cyber risk management regimes to keep them protected. To address this, NCSC has developed the Cyber Assessment Framework (CAF) to help achieve and demonstrate an appropriate level of cyber resilience in relation to certain specified essential functions performed by that organisation1.
Function of the CAF
The CAF was developed and is continually reviewed for use by the NCSC to align with the Government Cyber Security Strategy 2022 – 2030. It is not a solution to cyber security threats, but a tool organisations can use to strengthen their cyber resilience. The CAF is intended for organisations responsible for CNI, it can be tailored to be used by any organisation or business that handles sensitive data to be compliant with the government cyber policies. Organisations can conduct self-assessments or utilise external bodies (commercial services) to make CAF based assessments to measure cyber resilience and government compliance. In essence, the correct utilisation of the CAF will ensure an organisation has achieved the basic cyber hygiene and the ability to withstand specified categories of cyber threats.
Construct of the CAF
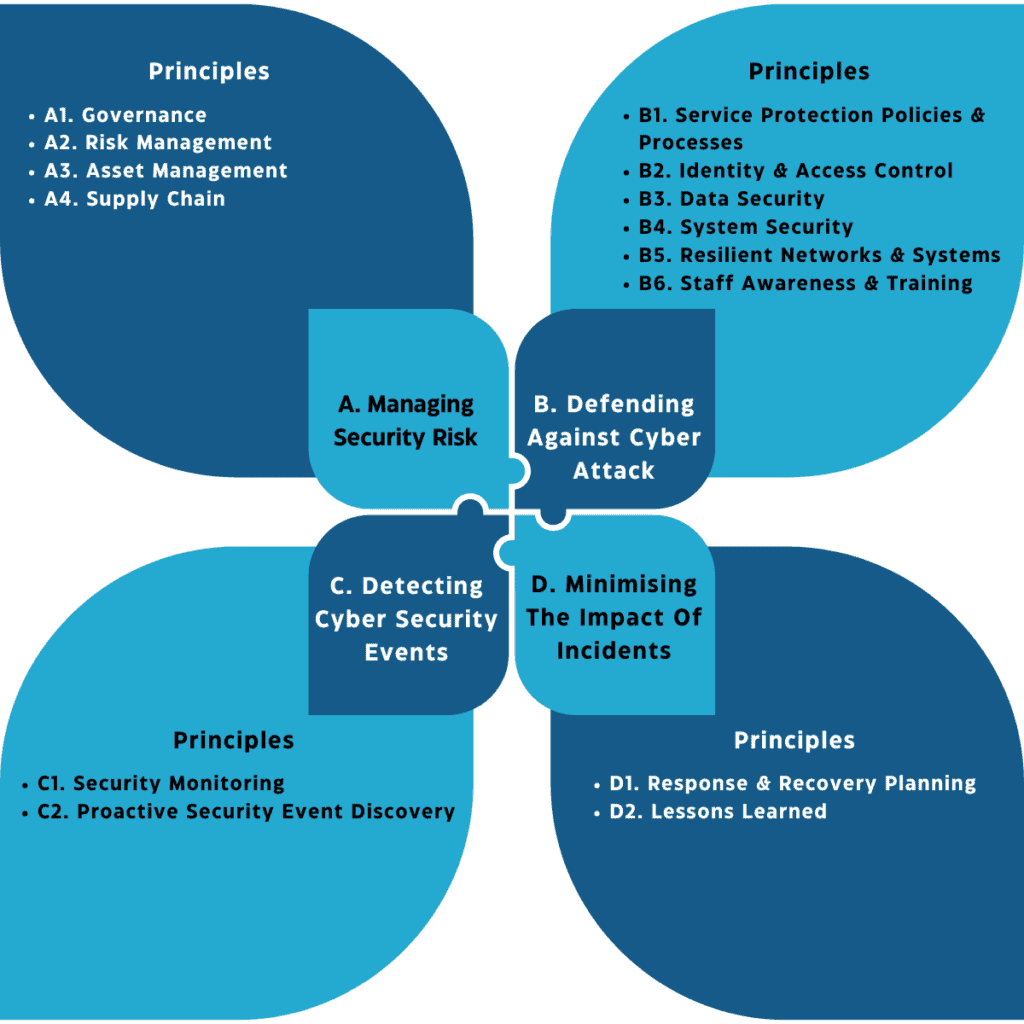
CAF objectives and guiding principles
At the first glance, the CAF may seem lengthy and complicated, however, it has been simplified by dividing into four main objectives and further sub-divided into sets of principles, fourteen in total, to guide the decision making process. The contributing outcomes (achieved, partially achieved or not achieved) of the principles are laid out with sets of indicators of good practices (IGP).
Objective A: Managing Security Risk
In order to fulfill Objective A, the CAF emphasizes that organizations must comprehend the possible cyber threats and the consequences of a breach. It is about knowing how to control and mitigate those risks through implementation of correct policies and procedures. This includes the requirement for continual assessment, identification and understanding the security vulnerabilities within the organisation, and risks that arise from the dependencies on external service providers. The guiding principles for achieving this objective include governance, risk management, asset management, and supply chain management.
Objective B: Protecting against Cyber Attacks
Objective B within the CAF has laid down six principles to achieve . This includes service protection policies and processes, identity and access control, data security, system security, resilient networks and systems, and staff awareness and training. In order to achieve effectiveness in protecting against cyber attacks organisations need to ensure appropriate policies, process and procedures are communicated and practiced. They need to understand the roles and responsibilities of the employees to implement appropriate access control and right level of administration rights to the essential functions. Data access needs to be based upon Least Privilege and the Need to Know principles and information should be appropriately managed. Any network or infrastructure build within the organisation should be built with security in mind which should be continually assessed and tested for cyber resilience. Most importantly, organisations must appropriately support and educate their staff and ensure they all understand and contribute towards making the organisation cyber secure.
Objective C: Detecting Cyber Security Events
This objective is based on two principles, security monitoring and proactive security event discovery. It focuses on organisations having the capabilities to quickly spot any unusual activity or potential cyber attacks on NIS through the use of monitoring tools and software. Organisations should be logging events and analysing them to understand trends of security threats. The correct implementation of the principles will enable the organisations to detect any malicious activity that can potentially harm the essential functions of the NIS.
Objective D: Minimising the Impact of Cyber Security Incidents
This part of the CAF is all about making sure the organisation can deal with an incident and recover quickly minimising impact on essential operational functions. It is also about reflecting on the incident and identifying the lessons learned to solidify cyber resilience to avoid future similar incidents. The guiding principles to achieve this are response and recovery plans and lessons learned processes. Organisations need to prepare, plan and practice simulating cyber attacks to validate these processes and procedures.
While the CAF was initially designed to support organisations enabling critical infrastructure, its principles can be applied to businesses of all sizes. By using the CAF, organisations can strengthen their cybersecurity and ensure compliance with government standards.




